There’s no need to reinvent the wheel, as we’ve often heard. To save time in their application development, many software publishers and companies use customizable software strains such as a web server or an application server to avoid starting from scratch. To keep costs down, most companies use open-source software because it’s available for free.

Open-source software is generally available in executable format, i.e. for installation on an operating system, as a virtual machine image, or in container image format for direct execution by solutions such as Docker, ContainerD, Kubernetes, etc. These open-source images are freely available to developers.
The use of open-source software solutions can unfortunately lead to unintentional security flaws, which can rapidly spread throughout the information system. These flaws can appear at the time of deployment, or after the fact, throughout the entire period of use. One of the best-known is the Log4j security flaw. Once a vulnerability has been detected, it must be quickly corrected to prevent it from becoming the vehicle for an attack and spreading.
An image is made up of an OS base and software. To counter security flaws, companies dedicate a team to building their own images. This team will first create the base, from an OS, purge it to leave only what is useful, then configure it as best as possible to limit attack surfaces, also known as a hardened OS. From this base, it will create an image by adding open source software and making it available to developers, either in an HTTP repository for VM images, or in a registry for container images.
As the appetite for open-source software is high and growing rapidly, this requires the construction of many images and therefore the involvement of many developers, who will spend less time on developments linked to the company’s business.
Tanzu solution portfolio improves developer productivity and also enhances security. VMware Application Catalog , built by VMware thanks to the acquisition of Bitnami by VMware in 2019 enables companies to achieve development agility by consuming open source images, while being confident about the level of security obtained, since they have been scanned and secured by VMware.
Firstly, the operator will be able to filter which open-source images can be consumed by developers. Secondly, the operator will be able to supply its own hardened (secured) OS base, or if it wishes, use those proposed by VMware. This OS base will be used by VMware Application Catalog for the automated construction of complete OS base + open-source software images. The image thus created will be automatically made available to developers in the registry chosen by the operator in the case of container images, or as a downloadable link in the case of VM images.
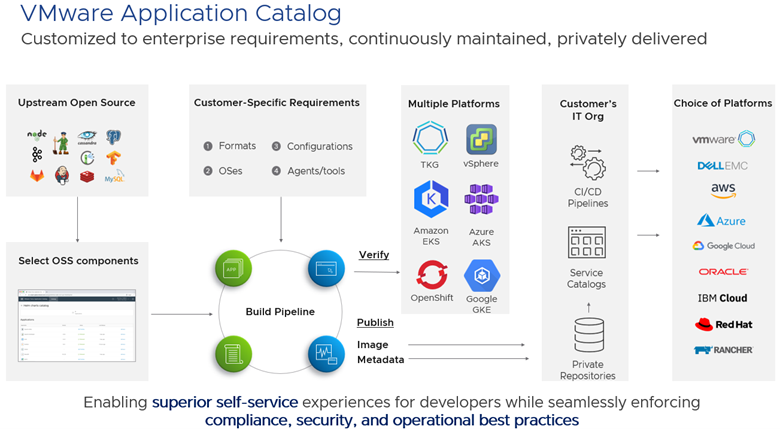
If a security breach is identified in one of the open-source software products or in the OS base, a new image is automatically recreated with the associated patch, and made available to developers without any intervention on their part.
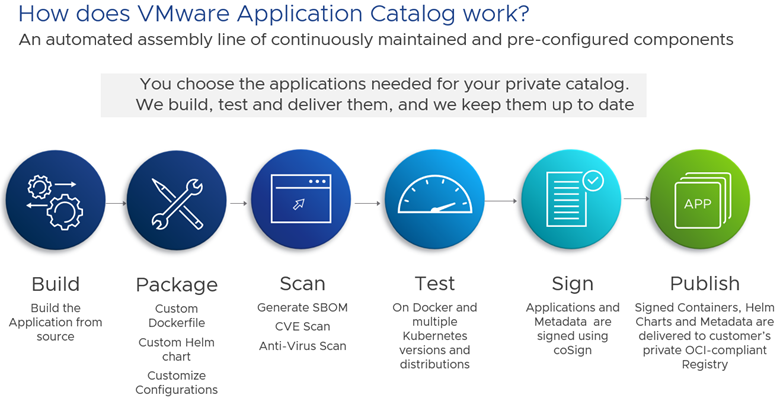
VMware Application Catalog improves development security and developer productivity, as they no longer have to create images and maintain them throughout their consumption lifecycle. They’ll have more time to devote to developments directly linked to their company’s business.
Imagine the savings in developer and operator time. Imagine also having a secure system where open-source software benefits from the same level of security as paid-for software. It’s rare that you can combine agility and security at the same time, as we generally find that the constraints imposed (but necessary) by security are unfortunately a brake on agility.
Leave a Reply